

Version Compatibility
We aim to keep our extensions always compatible with the latest stable versions of Magento. To ensure we keep our extensions as clean and fast as possible, we test our extensions on PHP 8.1 and up
We no longer test our extensions on PHP 7.x
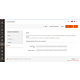
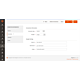
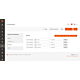
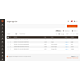
| Version | PHP Version | Open Source | Adobe Commerce |
|---|---|---|---|
| v2.4.8 | PHP 8.3 or higher | ||
| v2.4.7 | PHP 8.1 or higher | ||
| v2.4.6 | PHP 8.1 or higher |
Single Sign On
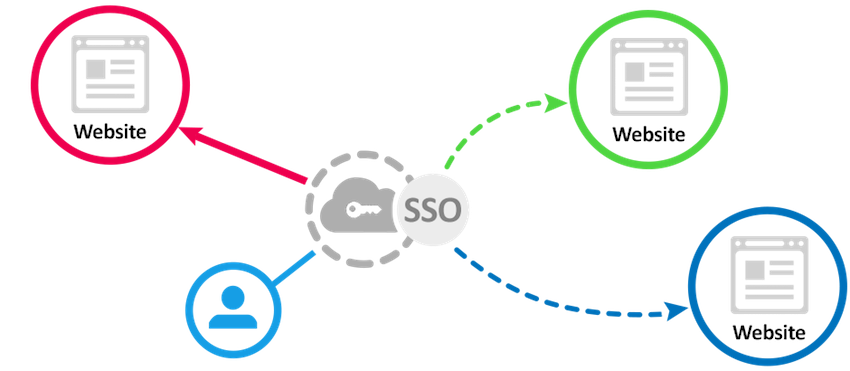
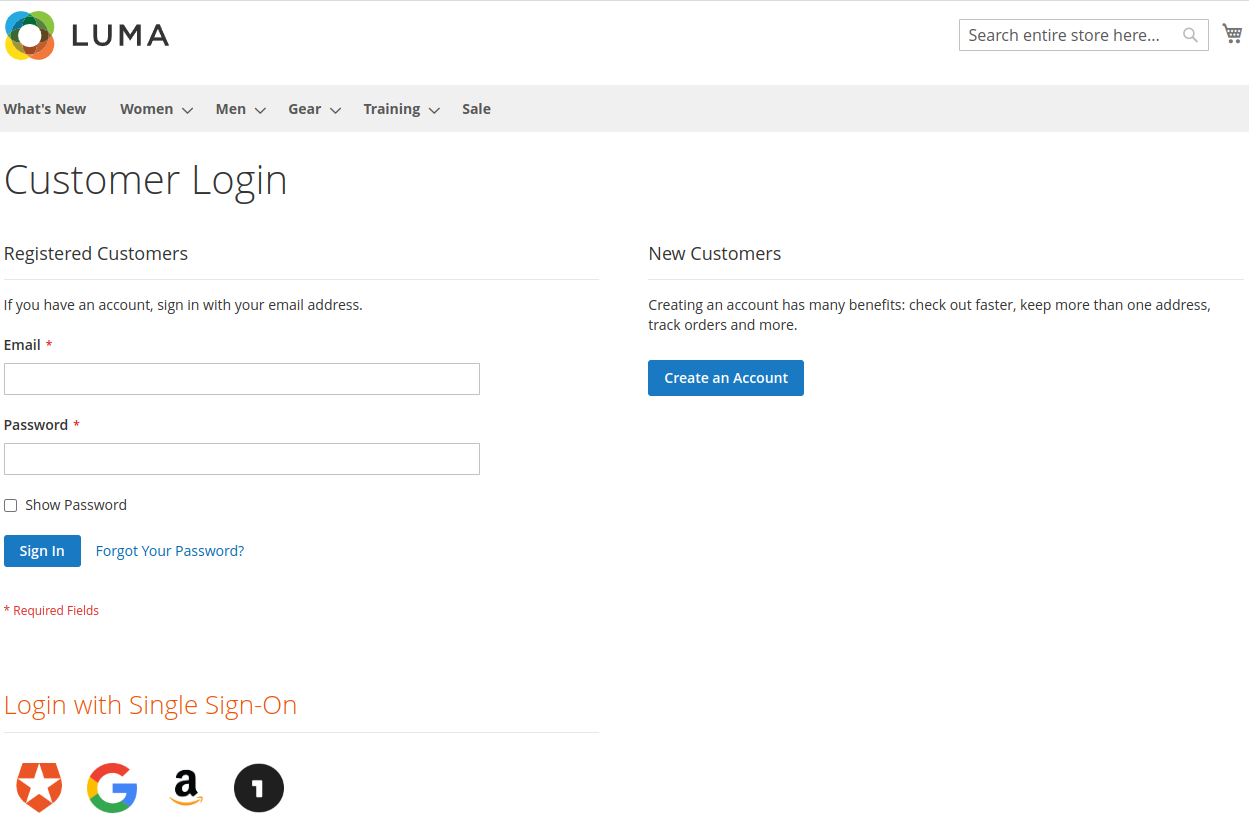
Our Single Sign-On extension for Magento 2 makes it easy for your customers and backend users to log in directly through your Identity Provider, without having to go through the account creation process. 100% Multi-Store compatible and simple to set up, this extension is a must-have for any Magento 2 store.
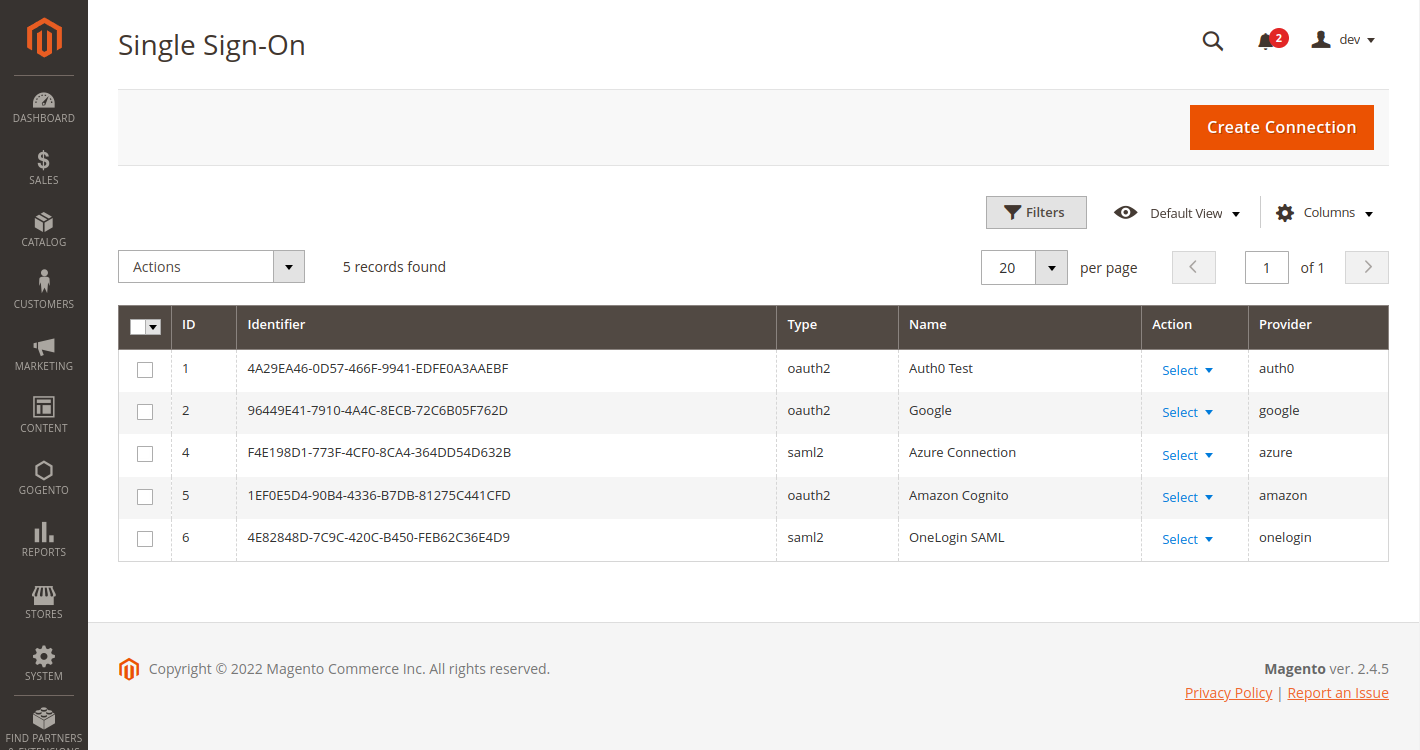
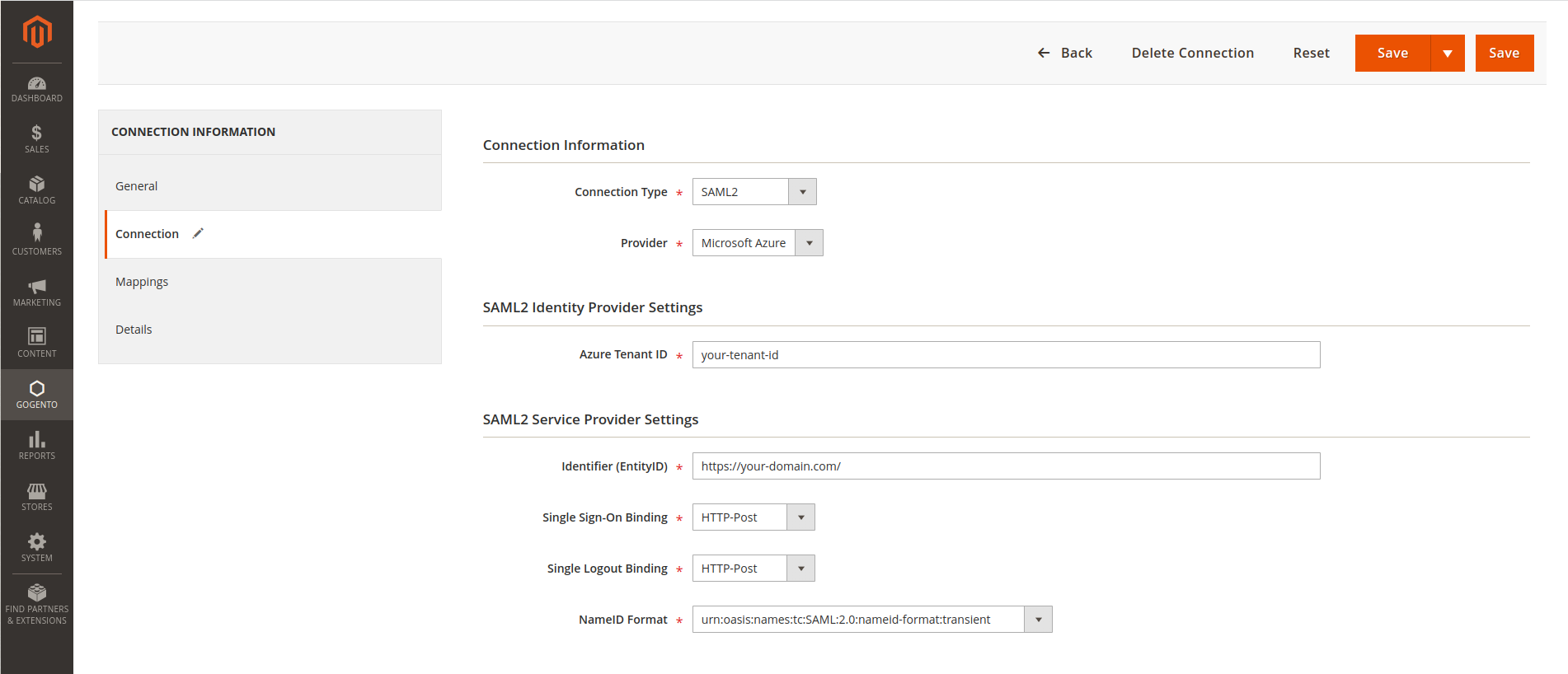
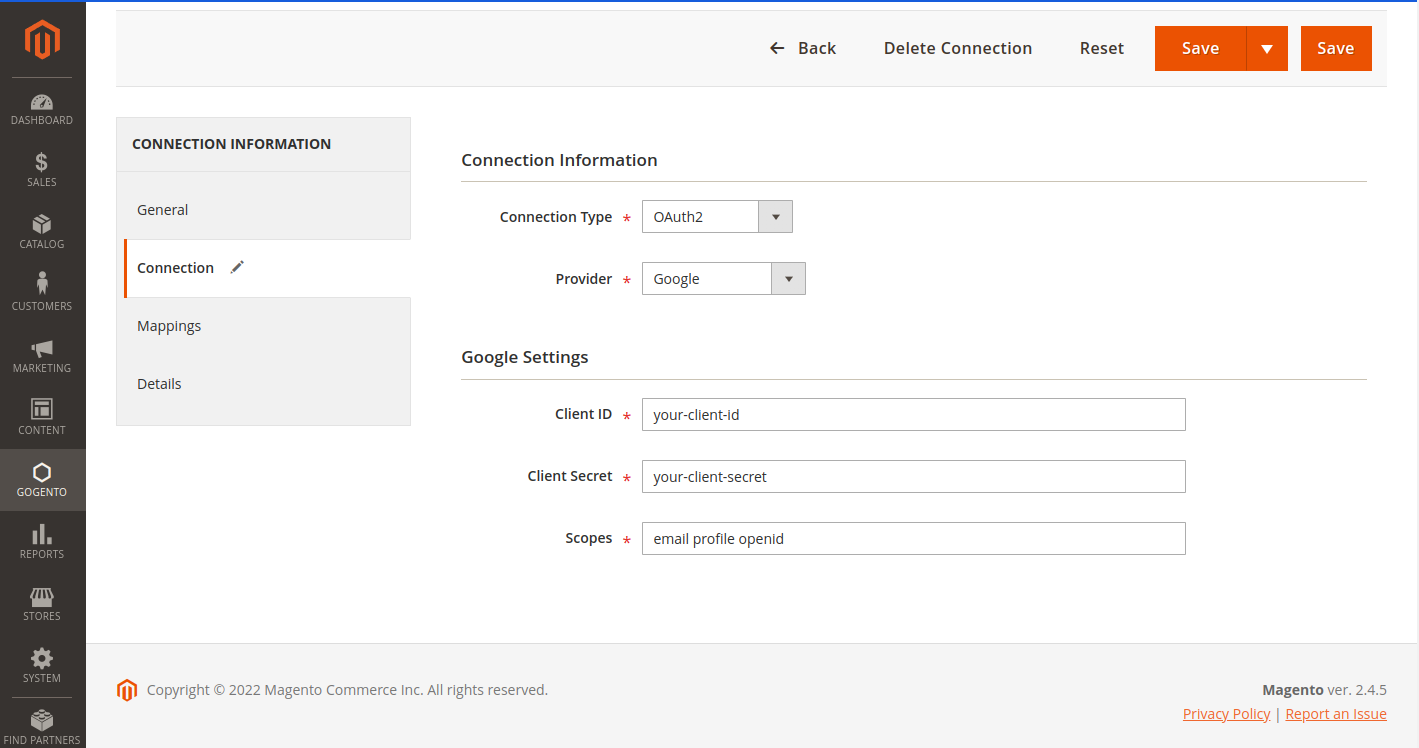
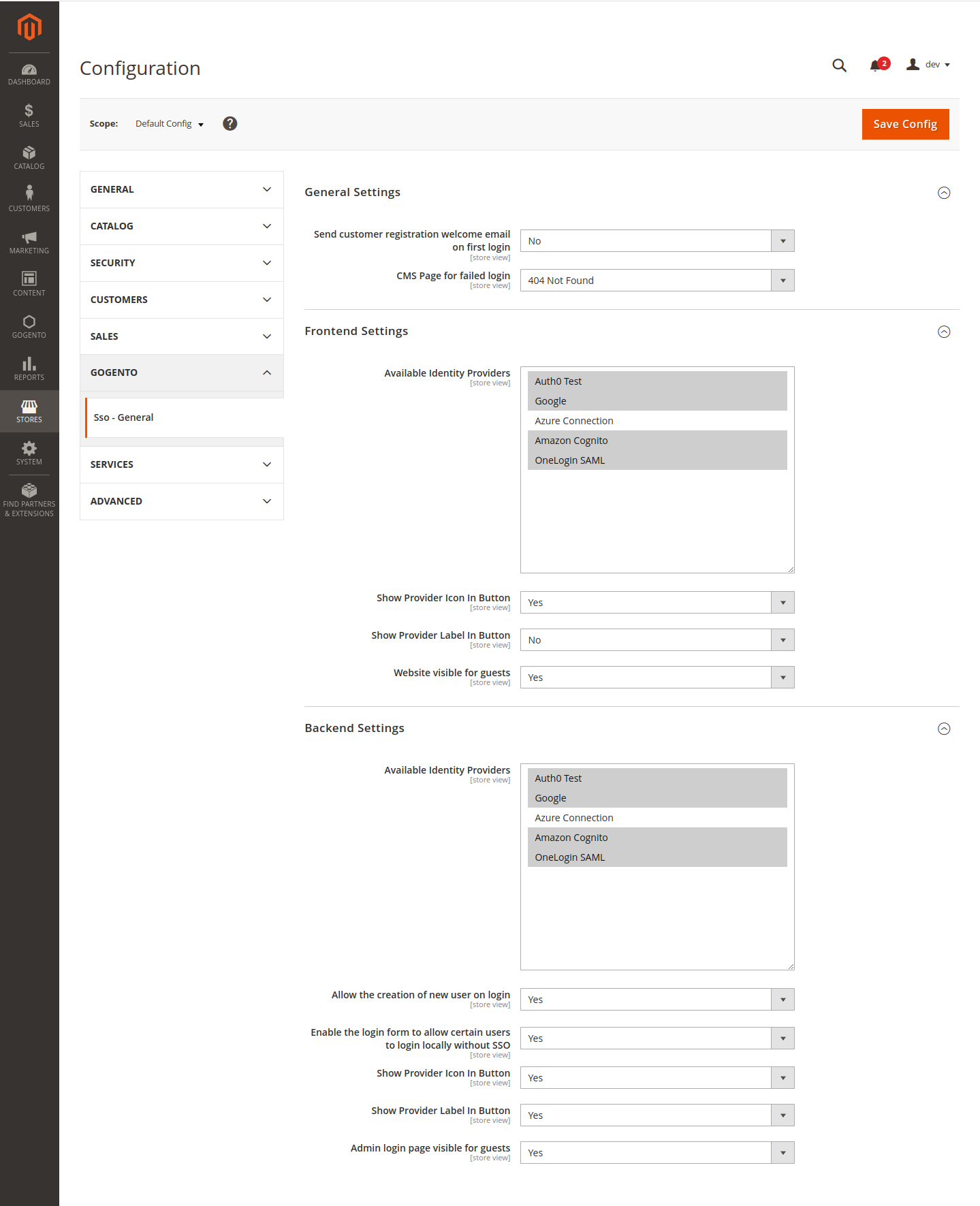
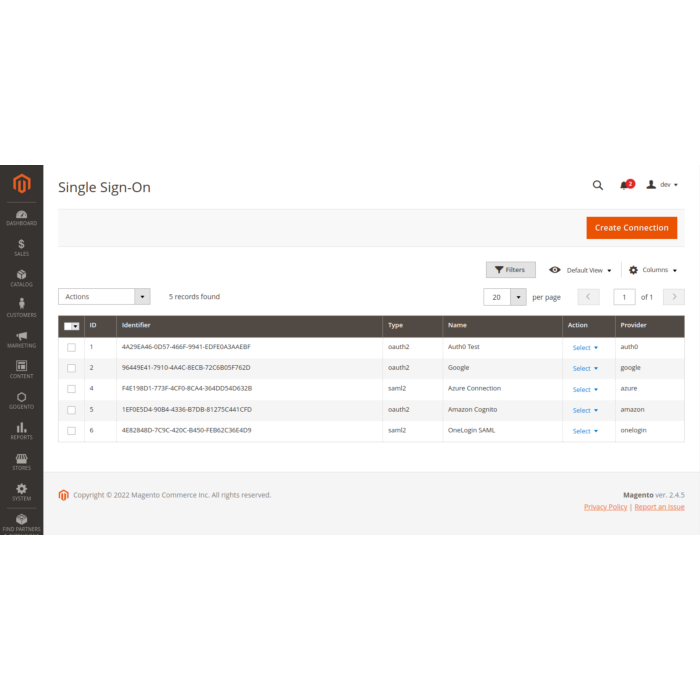
Compatible with both OAuth2 and SAML2 protocols, our extension is able to work with nearly any Identity Provider on the market. You can create multiple integrations from your Magento 2 backend, and easily switch between them for different websites.
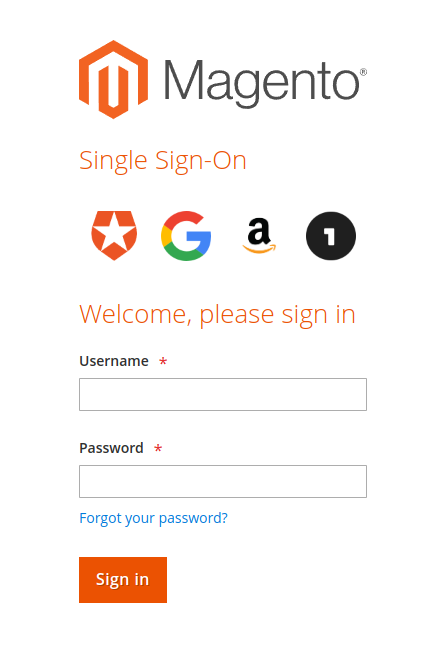
With our Single Sign-On solution, your customers and admin users will see a new login option on the login page, allowing them to log in with just one click. Upon successful login, they will be redirected to the shop and logged in automatically. If the user does not exist in the shop, an account will be created for them automatically.
Our Single Sign-On solutions have been successfully implemented in hundreds of webshops worldwide, including major brands such as Nokia, Canon, Castrol, Pearson, Dentons, and many more. We have gained invaluable experience from these implementations and are confident that our extension will be able to improve the customer experience and increase revenue for your webshop.
With our Single Sign-On extension, you can have your customers connected to your Single Sign-On environment in no time, and remove barriers to entry for your customers. Take the first step towards a more streamlined and secure login process for your Magento 2 store today.